Data Lifecycle and Security
Effective data lifecycle management is critical for maintaining security, compliance, and operational efficiency in semiconductor organizations. From the moment data enters your environment to its eventual retirement, comprehensive governance controls ensure sensitive information remains protected while supporting business objectives and secure data sharing.
Data Lineage and Provenance Tracking
Complete visibility into data movement and transformation provides essential security oversight. Palantir's permission checking capabilities include the Check access panel for validating user permissions, Data Lineage visualization for understanding access across complex data pipelines, and Access Graph for exploring relationships between projects, users, groups, and markings.
Lineage security features encompass:
- Visual representation of user access rights throughout complex transformation workflows
- Automatic identification of security classifications that flow through data lineage
- Clear understanding of data sharing boundaries and access requirements when collaborating with other organizations
- Dynamic checking of user permissions against direct access requirements and inherited data requirements
- Understanding how permission changes upstream affect access to downstream datasets and analytical outputs
Sensitive Data Detection
AI-powered sensitive data identification through the Sensitive Data Scanner automatically discovers and protects sensitive information throughout the platform. This proactive approach ensures sensitive data receives appropriate protection regardless of how it enters the system.
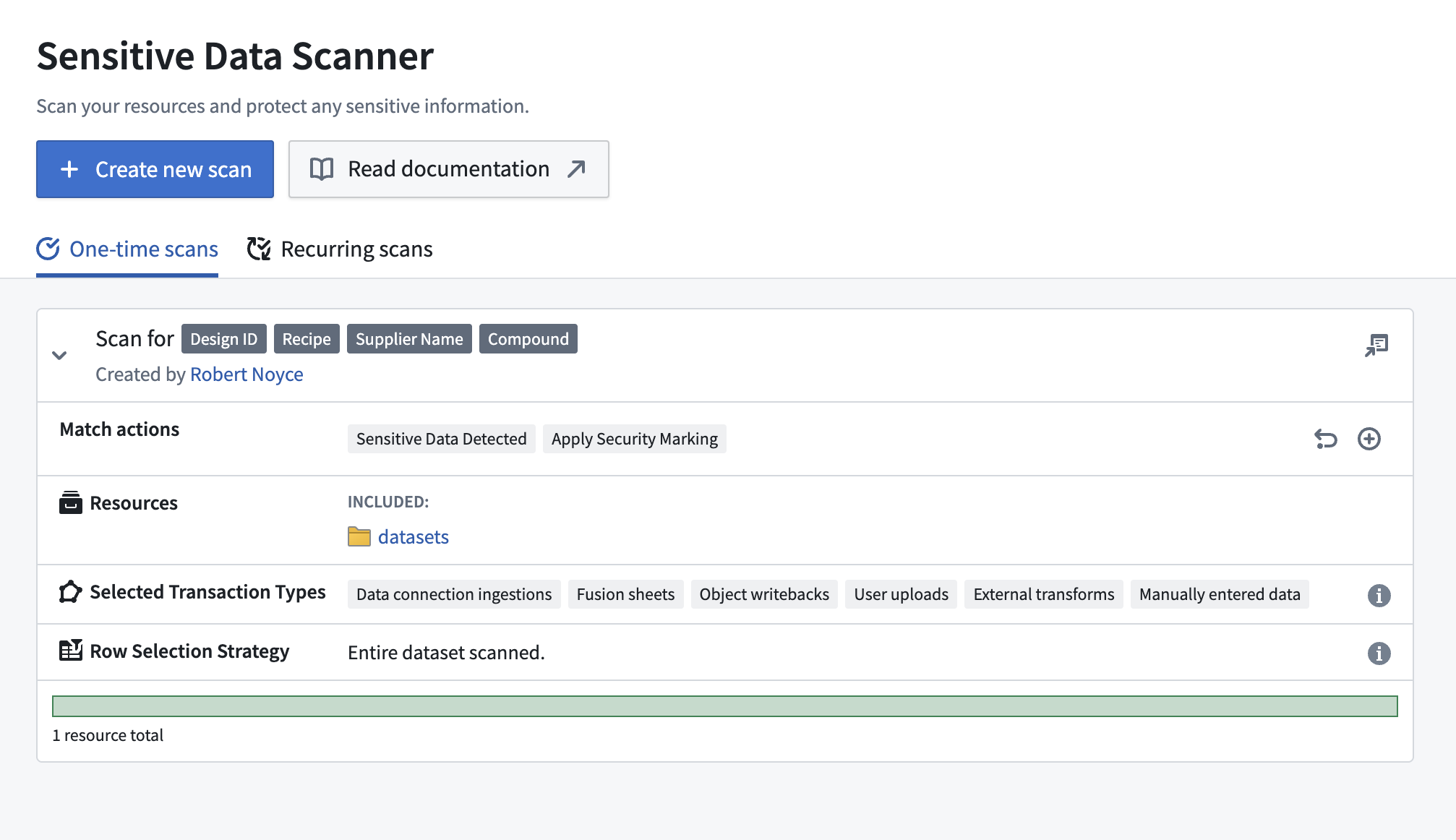
The scanner provides semiconductor-specific detection for:
- Fab process parameters and proprietary manufacturing recipes
- Customer-specific part numbers and technical specifications
- Financial information including pricing models and cost data
- Names of chemical compounds or precursors in development
Pattern recognition capabilities extend beyond standard PII detection to identify industry-specific sensitive information, with automated masking and real-time exposure risk alerts.
Approval Workflows
Multi-level authorization ensures sensitive operations receive appropriate oversight before execution. The Approvals system integrates with existing governance processes while providing semiconductor-specific workflow capabilities.
Workflow capabilities include:
- Configurable approval chains for different types of sensitive operations
- Integration with existing enterprise governance processes
- Complete audit trails for regulatory compliance and internal oversight
Semiconductor-specific workflows address unique industry challenges such as IP release approvals for collaborative projects, data sharing agreements with suppliers, and export control compliance verification.
Checkpoint Controls
Automated validation points throughout data pipelines ensure security and quality standards are maintained. Checkpoints provide configurable gates that validate data integrity, security posture, and compliance requirements before allowing processing to continue.
Security checkpoint features:
- Automated security scanning at each pipeline stage
- Data quality verification before cross-organizational sharing
- Compliance validation against industry-specific standards
- Configurable failure handling and escalation procedures
Automated Data Management
Comprehensive data lifecycle management through Data Lifetime ensures information is retained appropriately and disposed of securely when no longer needed. This automated approach reduces compliance risk while minimizing storage costs.
Lifecycle management capabilities:
- Configurable retention periods based on data classification and business requirements
- Legal hold capabilities for litigation support and regulatory investigations
- Secure data destruction with certified erasure and compliance documentation